Encryption symmetric Encryption and decryption in c#. encryption is the process of… Sixth chapter lesson-10: database security.
A Quick Guide to Encrypted Messaging | Network Wrangler – Tech Blog
What is encryption? definition, types, uses and more Encryption tls decryption Encryption types symmetric asymmetric hash algorithm aes key vs algorithms hashing encoding project obfuscation pki security cryptography computer data example
Data encryption
Encryption hashing differences okta definitionsEncryption end infographic encrypted computer security apps messaging explained work works does visit use technology should science io guide source Encryption bit softwareEncryption data key authentication digital code using public advanced rsa signing state way nuget package security powershell enterprise improve accounts.
Symmetric encryption 101: definition, how it works & when it’s usedEncryption does mean asymmetric symmetric vs why algorithm important file Beginner's guide to encryptionBest and worst practices for tls/ssl.

Cybersecurity encryption background threats strengthen proactive biggest vereist encryptie verbinding concept attacks devops affari protects vectra azure extends ufficio finanziari
What does encryption mean and why is it important?Encryption matlab aes decryption Image encryption and decryption using aes algorithm matlab source codeEncryption decryption encrypted encrypt decrypt hashing ciphertext salting cloudsoft frameworks wondering exactly might examinations.
Encryption advanced standard security network aes software development tutorials tutorialSymmetric encryption 101: definition, how it works & when it’s used Encryption decryption cipher sixth edupointbdAdvanced encryption standard.

Encryption symmetric works definition used example using when graphic aes shows security
7.07 cryptography: securing the internetKeeping data safe: introduction to encryption 16 best 256-bit encryption software to protect your filesEncryption stormagic.
Encryption data cryptography recovery decryption key api advertising amazon internet securing file encryptedCommonly used encryption algorithms A quick guide to encrypted messagingEncryption protect oleksandr.

Hashing vs. encryption: definitions & differences
.
.


Beginner's guide to encryption

Symmetric Encryption 101: Definition, How It Works & When It’s Used

Commonly used Encryption Algorithms - Kruptos Security Blog
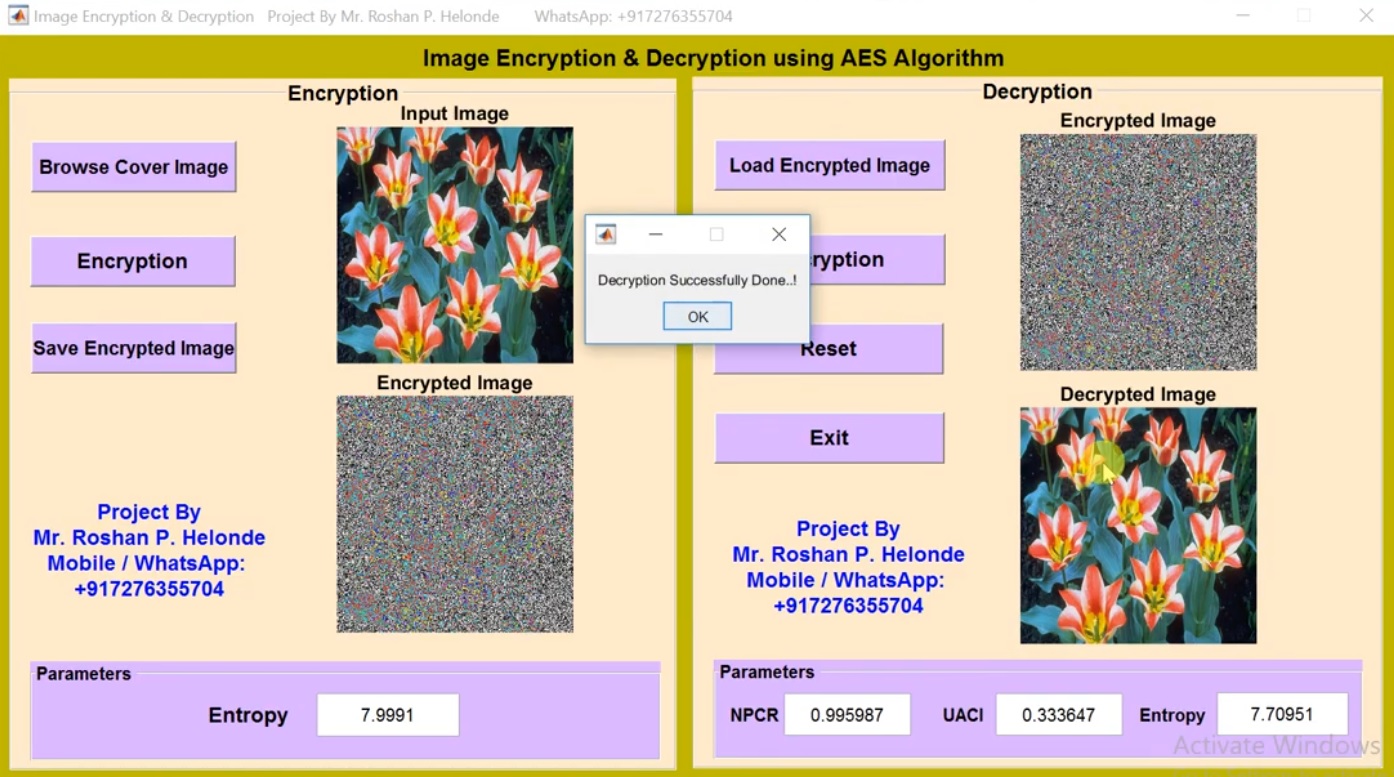
Image Encryption and Decryption Using AES Algorithm Matlab Source Code

Best and worst practices for TLS/SSL

Advanced Encryption Standard | Comprehensive Understanding of AES

Encryption and Decryption in C#. Encryption is the process of… | by

A Quick Guide to Encrypted Messaging | Network Wrangler – Tech Blog
